Custom auth token
Generic authentication serves as an alternative for those using their own authentication server. This method accommodates various authentication types not currently supported, such as GitHub, or custom systems.
Essential steps and requirements for generic authentication through an endpoint include:
- Post-login, generate a public identifier to recognize the user
- Relay this identifier to the private key to initiate wallet creation
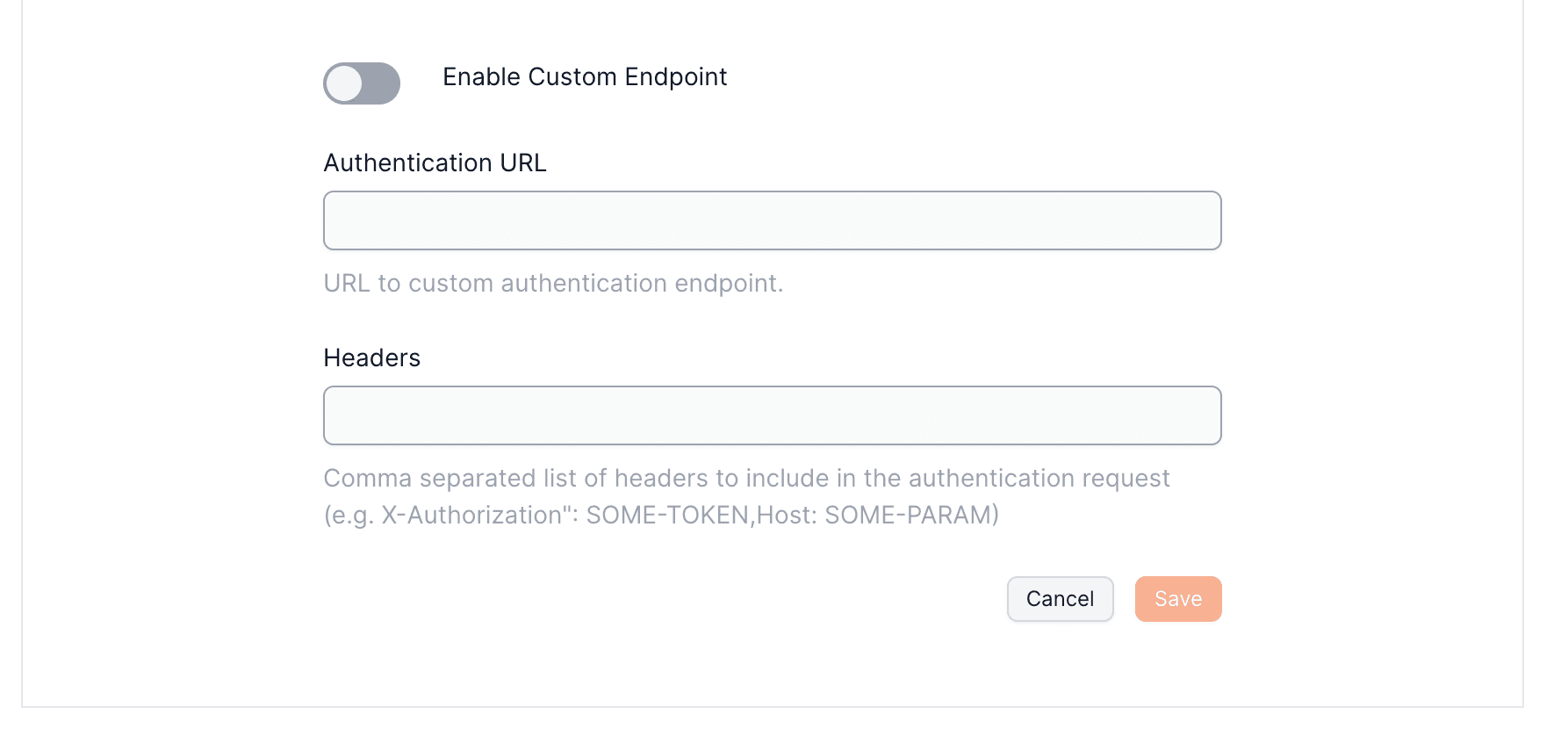
- An endpoint you provide is contacted to confirm the user's identity, upon which Openfort creates a wallet if the information is valid
Supply an endpoint for identity verification. Additional headers for request authentication can be passed and accompany every verification request to your endpoint.
Authenticating users with generic authentication
Configure your server
Within the server that handles authentication requests, implement an endpoint responsible for verifying the user's identity. This endpoint should accept a POST request with a JSON body containing the payload field, which corresponds to the user's public identifier.
{
"payload": "public_identifier"
}After returning a JSON response, the SDK creates a wallet for the user if the response is valid. The response should contain the following fields:
{
"userId": "unique_user_id",
"email": "user_email"
}Set up your provider
To set up your Custom Authentication with Openfort, visit your dashboard provider settings.