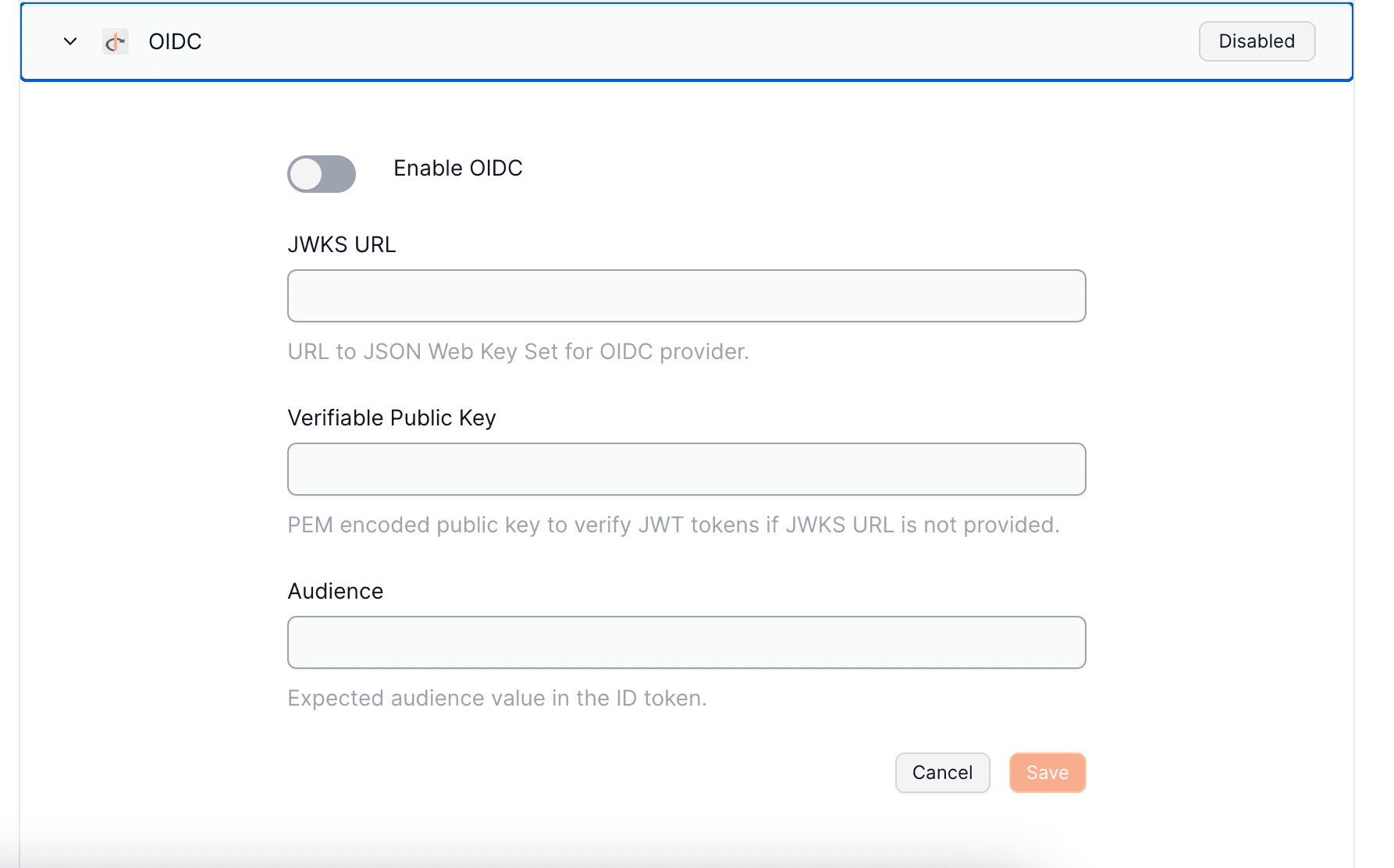
Custom OIDC auth
OIDC authentication is a viable choice when using an external authentication provider such as Auth0 or Cognito that offers JWK publication for token authenticity verification.
An OIDC authentication framework employs a public-private key pair, utilizing the private key to sign authentication tokens. The public key is made accessible via a public URL in JWKS format, typically found at https://{domain}.com/.well-known/jwks.json. When a user logs in, an idToken (a JWT) is produced and signed with the private key, following OIDC specifications for token field requirements. This JWT is then used within the private key to create a user wallet.
The verification of the JWT against the public key confirms its authenticity, allowing wallet generation based on the subject (user identifier) within the idToken.
Input requirements
- JWKS File URL (public key): Validates the token's authentic signature
- idToken's
audvalue: Confirms that the intended recipient of the token is correct
Authenticating users with OIDC-compatible authentication
Set up your provider
To set up your OIDC Authentication with Openfort, visit your dashboard provider settings.